Integrating Control Center with LDAP Service
Lightweight Directory Access Protocol (or LDAP) is a software protocol that enables you to store information about the structure of your organization in a specially structured way. LDAP configuration is organized in a tree-like hierarchy that includes the following items that can be optional:
-
Root directory: Where we begin looking for the information in the LDAP tree;
-
Common name (CN): Used for storage of people’s names, product names, job titles, and so on;
-
Organization (O): The name of an organization. Used as a top-level item (root);
-
Organization unit (OU): The name of a unit or team in the organization;
-
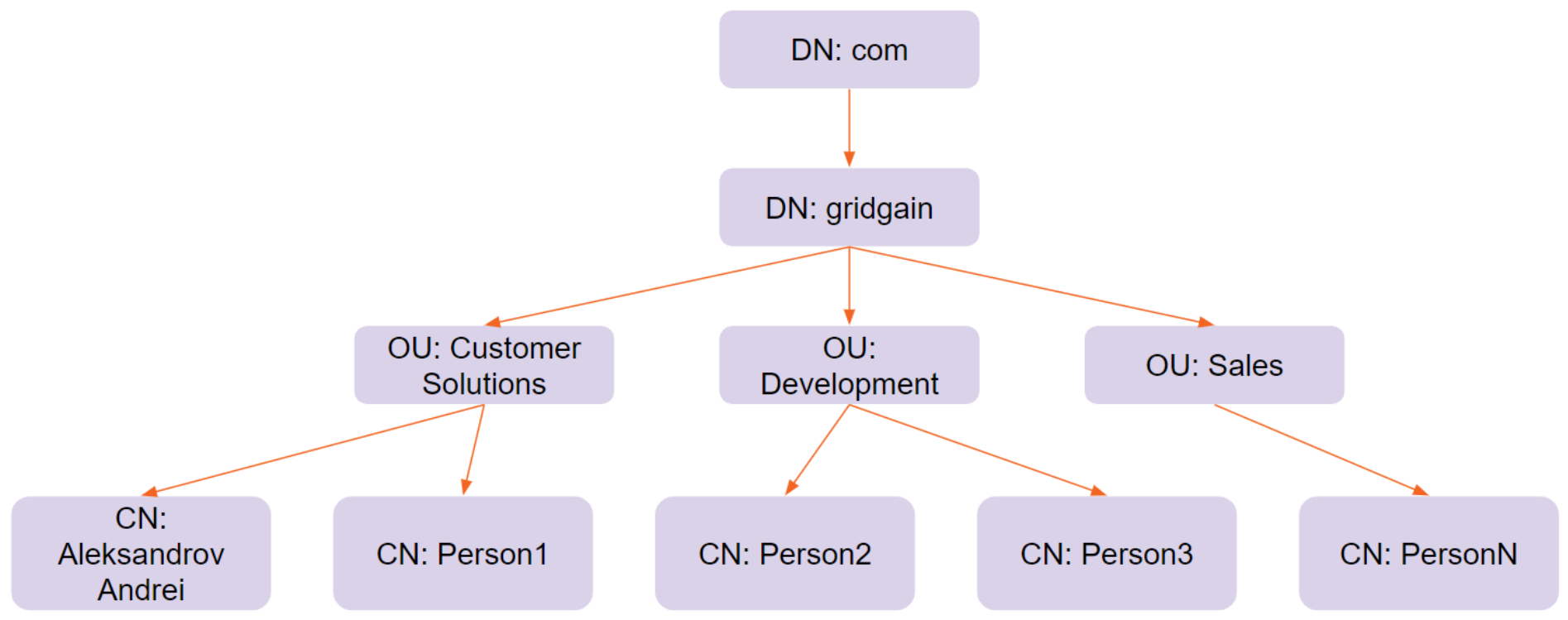
Domain name (DC) or Domain component (DN): Usually points to some kind of DNS-based LDAP tree that has the following style - CN=Aleksandrov Andrei,OU=Customer Solutions,DN=gridgain,DN=org
These are the items that you are most likely to use. However, there are more items, such as country (C) and street (S).
CN=Aleksandrov Andrei,OU=Customer Solutions,DN=gridgain,DN=org must be read from right to left and it can be represented in the following LDAP tree:
Now, let’s see how LDAP is used:
-
Usually, LDAP is used for authentication and authorization processes. It has several mechanisms:
-
The process of verifying a username and password combination (by using a directory server such as MS Active Directory or OpenLDAP) can be implemented via various protocols:
-
Anonymous: When neither a username nor a password is required;
-
Username/Password: When both a username and password are required;
-
Simple Authentication and Security Layer: A subset of protocols that can be used for authentication. For example, GridGain uses Java Authentication and Authorization Service (JAAS) to access LDAP login modules that can connect via SASL;
-
Generic Security Services API (GSSAPI): Protocols that can be used for SSO access. For example, Kerberos authentication servers can be used for login. If JAAS is used for Kerberos, an additional login module should be set.
-
-
When authorization is complete, user roles or permissions can be checked, to enable granting of special application-level permissions.
-
-
LDAP can be used as a data store, and various applications can connect to it to retrieve information about the structure of the organization and to store files. However, the tutorial does not cover this use case.
Thus, authentication and data searching are two of the operations that can be performed in LDAP. Let’s look more closely at the search operation.
For every search, the following parts should be configured:
-
Information about the authentication mechanism and user credentials: Both are required;
-
Search base: The place in the LDAP tree from which the search should be performed;
-
LDAP address: The host and port of the LDAP server;
-
LDAP search filter: Filters are used to limit the number of users or groups that are allowed to access the application or to build the authorization system (based on the roles that are applicable to the filters). You can read more about this model in the Role-based Authorization with Active Directory for GridGain article.
Additional features can be used for search, but we do not cover them in this tutorial. We are ready to integrate GridGain Control Center with LDAP.
OpenLDAP Server Configuration
In our example, we use the OpenLDAP server. You can read about the server on the OpenLDAP website.
To simplify the process, we use Docker images with OpenLDAP service. For configuration of the OpenLDAP server on a Windows host, you complete the steps below. The steps for other operating systems are similar:
-
Install Docker for Windows;
-
When installation is complete, install the LDAP viewer. The viewer can be any tool that enables you to view and modify the LDAP structure. If possible, you should use a tool that can work with LDIF files, because we will use LDIF files later. For example, it can be http://jxplorer.org. However, you can use the CMD interface instead.
-
Prepare the structure of your LDAP tree and store it to the
gridgain.ldiffile.# # Copyright (C) GridGain Systems. All Rights Reserved. # _________ _____ __________________ _____ # __ ____/___________(_)______ /__ ____/______ ____(_)_______ # _ / __ __ ___/__ / _ __ / _ / __ _ __ `/__ / __ __ \ # / /_/ / _ / _ / / /_/ / / /_/ / / /_/ / _ / _ / / / # \____/ /_/ /_/ \_,__/ \____/ \__,_/ /_/ /_/ /_/ # dn: ou=people,dc=gridgain objectclass: top objectclass: organizationalUnit ou: people dn: uid=bob@control.local,ou=people,dc=gridgain objectclass: top objectclass: person objectclass: organizationalPerson objectclass: inetOrgPerson cn: Bob Hamilton sn: Hamilton uid: bob@control.local userPassword: bobspassword dn: uid=ben@control.local,ou=people,dc=gridgain objectclass: top objectclass: person objectclass: organizationalPerson objectclass: inetOrgPerson cn: Ben Alex sn: Alex uid: ben@control.local userPassword: benspassword dn: ou=groups,dc=gridgain objectclass: organizationalUnit objectclass: top ou: groups dn: cn=user,ou=groups,dc=gridgain objectclass: groupOfUniqueNames objectclass: top cn: user uniqueMember: uid=ben@control.local,ou=people,dc=gridgain uniqueMember: uid=bob@control.local,ou=people,dc=gridgain dn: cn=admin,ou=groups,dc=gridgain objectclass: groupOfUniqueNames objectclass: top cn: admin uniqueMember: uid=ben@control.local,ou=people,dc=gridgainThis structure has two users (
BenandBob) and two groups (adminanduser). Both Ben and Bob are in the user group. But, only Ben is in the admin group. Later, we will see why the users are treated differently. -
Start the OpenLDAP server by using the following command:
docker run -p 1389:1389 -p 1636:1636 --env LDAP_ADMIN_USERNAME=admin --env LDAP_ADMIN_PASSWORD=admin --env LDAP_ROOT=dc=gridgain --env LDAP_CUSTOM_LDIF_DIR=./ldif --name openldap bitnami/openldap:latest -
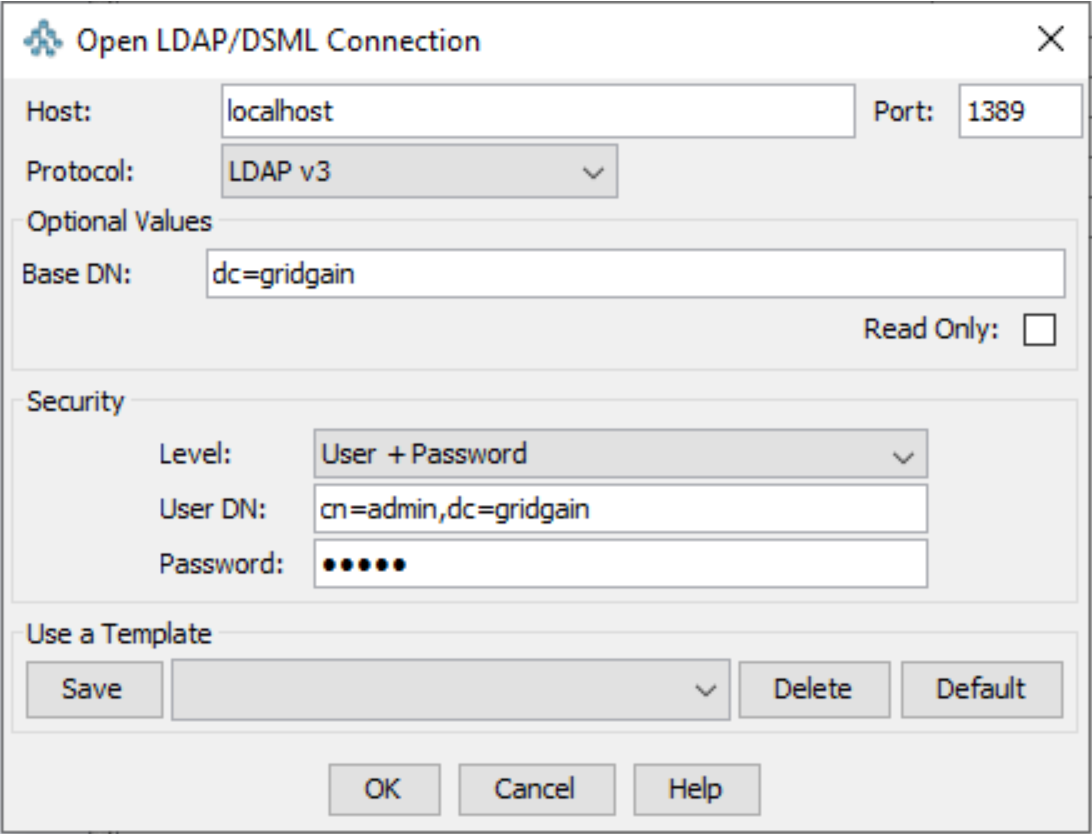
Under administration permissions, start the JXplorer tool and connect to the LDAP server as shown in the following screenshot (where the password is admin):
-
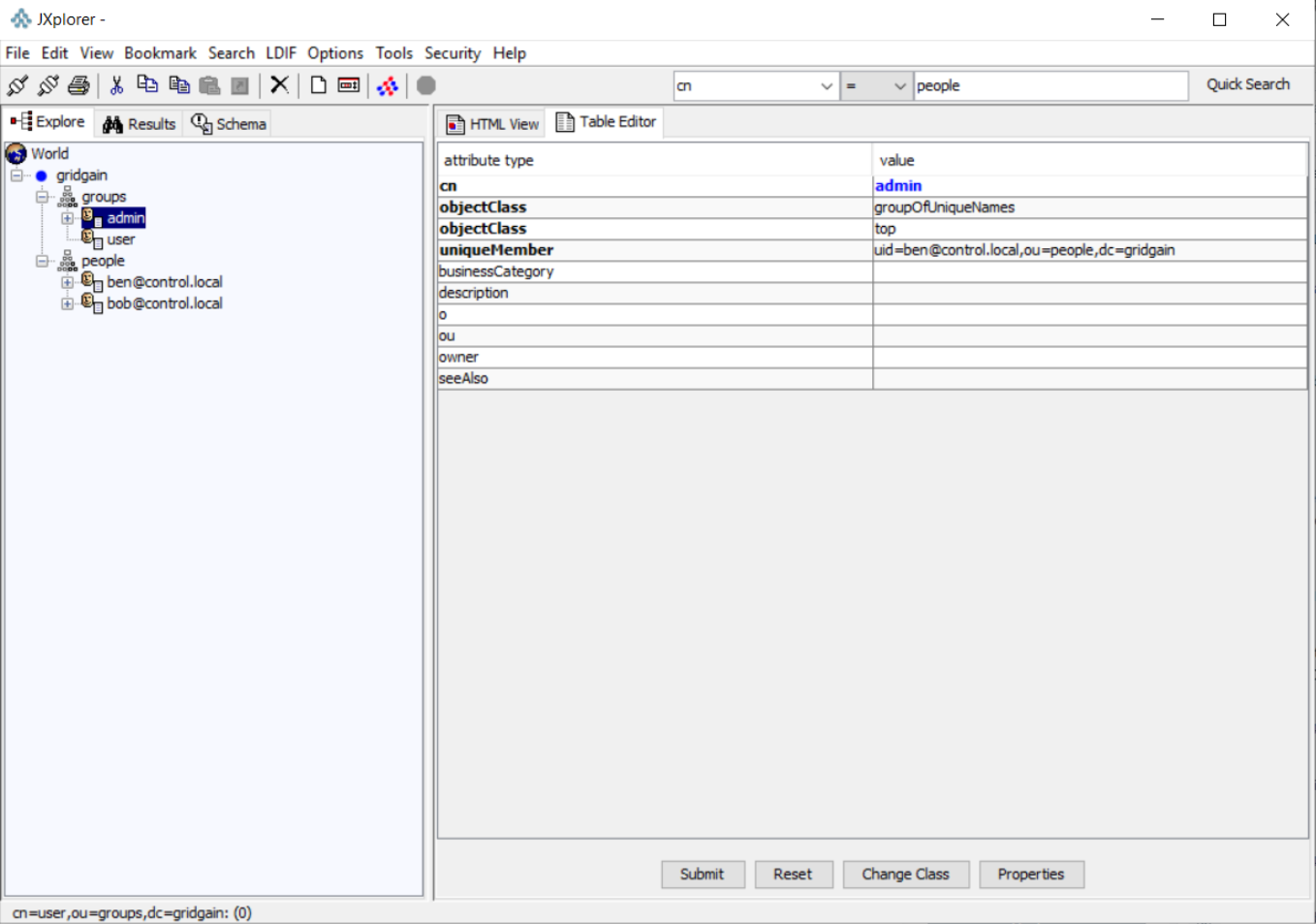
View the structure of the LDAP tree:
-
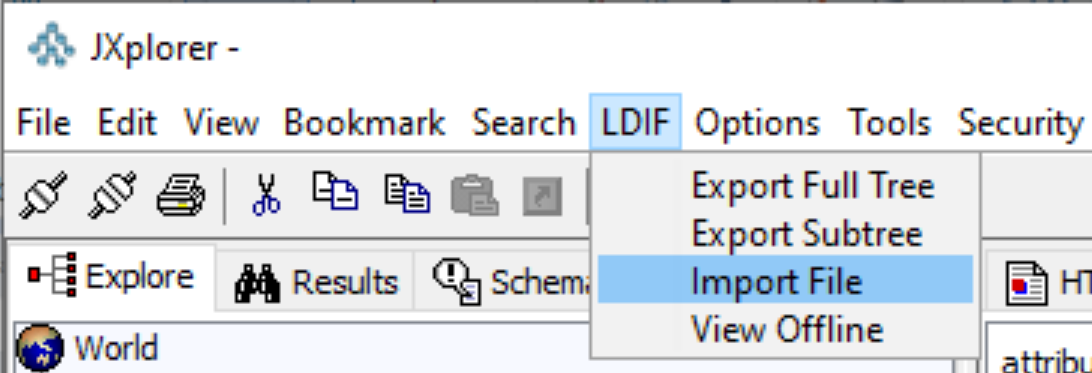
If you see an empty structure or different structure, delete the existed structure and manually import the settings from the ldif file:
That is how you configure the LDAP server.
Configuring Control Center
Now, you configure Control Center:
-
Download and unzip the Control Center binaries;
-
Navigate to the root folder of the unzipped directory and create an
application.yamlfile:spring.ldap.urls: ldap://localhost:1389 spring.ldap.base: dc=gridgain control.metric-collector.limitEnabled: true spring.ldap.user-details.groupSearchBase: "ou=groups" spring.ldap.bind-authenticator.enabled: true spring.ldap.admin-role: admin spring.ldap.user-details.groupRoleAttribute: cn spring.ldap.user-details.groupMemberAttributeName: uniquememberYou are required to add a special URL to connect to the OpenLDAP server and start the Control Center. Control center will perform the following:
-
Authentication with the username and password that you provide in the Control Center UI
-
An LDAP search that determines whether the current user is a member of the admin group
-
-
Start Control Center by using the
control-center.shscript; -
Move to the Control Center UI and click the SIGN IN button.
Now, you should be logged in using Ben and Bob accounts.
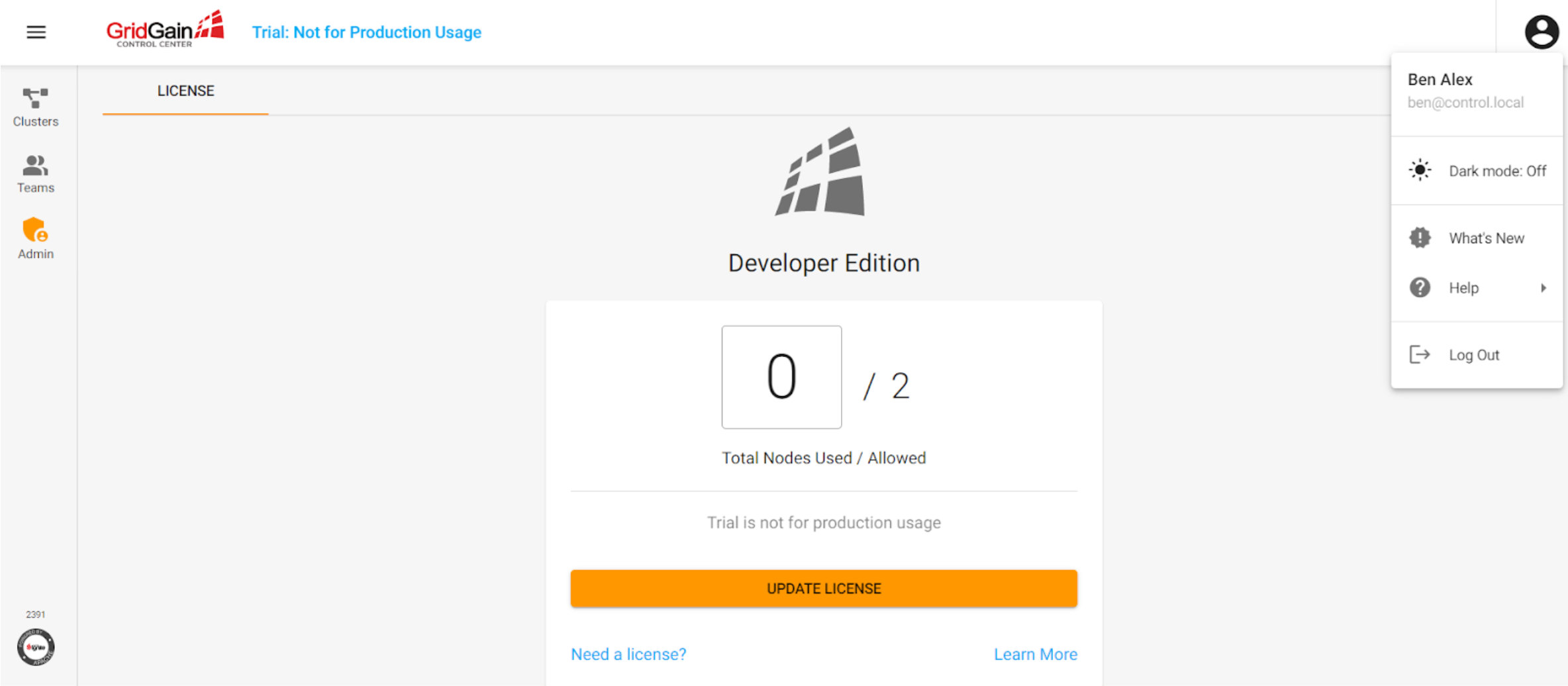
Ben’s account can see the following UI:
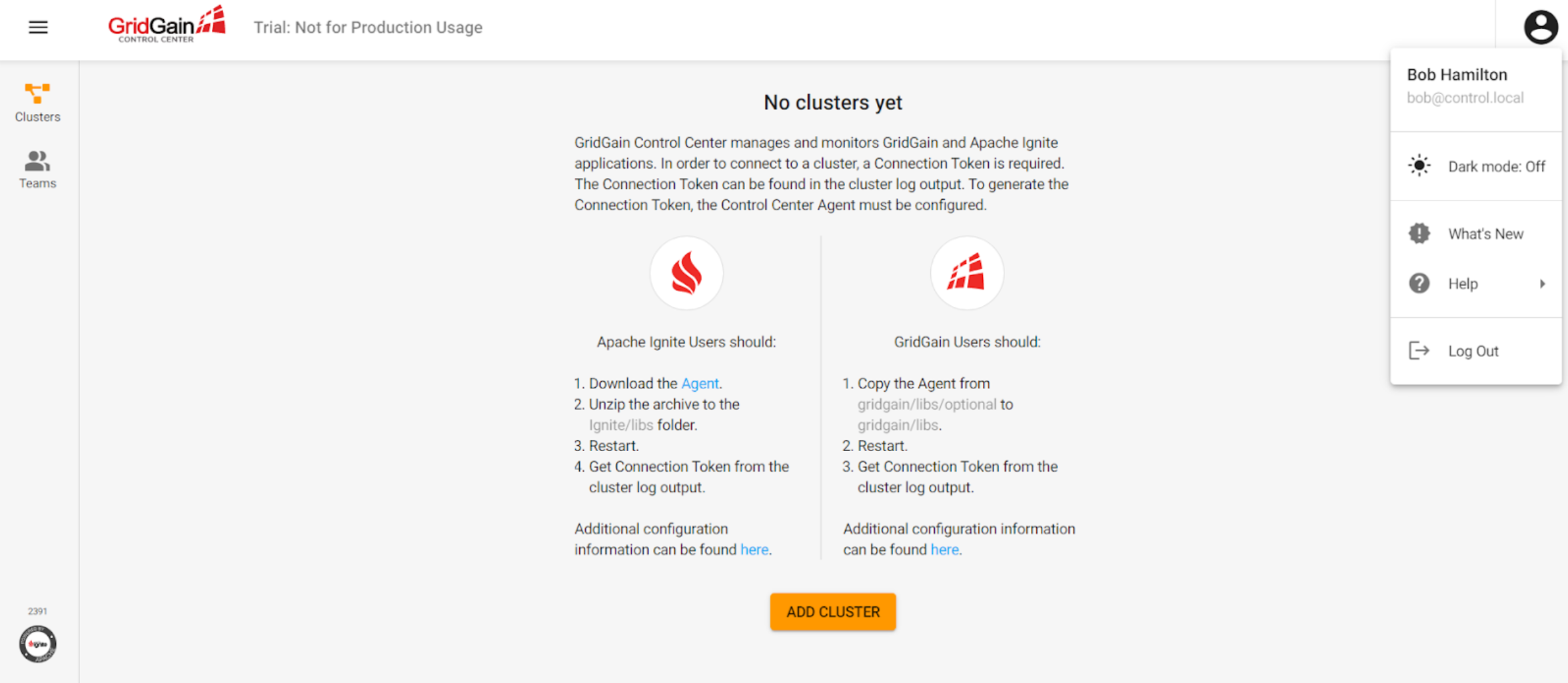
And, Bob’s account will be able to see the following UI:
As you see, Ben has a special admin panel that provides additional functionality.
© 2025 GridGain Systems, Inc. All Rights Reserved. Privacy Policy | Legal Notices. GridGain® is a registered trademark of GridGain Systems, Inc.
Apache, Apache Ignite, the Apache feather and the Apache Ignite logo are either registered trademarks or trademarks of The Apache Software Foundation.